Data theft through phishing
Cybercrime in Austria continues to rise in general. This was already shown in the last cybercrime report from the Federal Ministry of the Interior. The annual statistics on cybercrime (Statista) show a 5% increase in phishing, hacker attacks and data theft in Austria and a 4% increase in ransomware. In total, millions are lost through conventional or newly developed phishing attacks and those affected literally pay a high price. Phishing is the most frequent victim.
Criminals obtain personal login details in order to access their victims' online accounts. Do you use secure passwords on the Internet? Beware of phishing attacks, because even the most secure passwords won't help! We show in detail how phishing works, case studies and typical characteristics to be able to recognise phishing. And finally, what to do if you have fallen into the trap.
What is phishing?

We know hackers from films and how they use virtuoso programming skills and sophisticated technology to break into protected systems. In reality, however, data theft is usually much simpler. Online fraudsters mislead their victims and gain access to the victim's account or customer portal, usually without using any particularly advanced methods. Phishing is therefore the most widespread form of so-called social engineering attacks. Attackers pretend to be someone else, abusing either the victim's curiosity or the credibility of the brand or person they are impersonating.
The phishing process takes place in two parts:
Procedure of the phishing method
1.
First of all, cyber criminals send messages via email, social media or mobile phones as a lure. They are fake notifications and look deceptively similar to those from well-known companies or public organisations. Some people take the bait, follow the important-sounding instructions in the message and fall for the criminals. In more primitive phishing attacks, where the attackers only have email addresses or telephone numbers, a rather clumsy attempt is made to address as large a target group as possible.
However, if the contacts come from illegally obtained address databases, the automatically generated mass emails are sent with a personalised address. More detailed data from the target person, for example from a leaked customer database, adds real fragments of information to the deceptive message so that it is not ignored. This is becoming more and more common in view of the large number of traces we leave behind online as digital consumers.
If a pre-selected small group of people or individuals are also targeted in order to steal certain account passwords or financial data, this is known as spear phishing. Such a more targeted message appears more credible as it contains striking details about the victim. Attempts are made to reinforce this deception with fake but important-sounding file attachments (e.g. invoices) or by mentioning acquaintances or recent events from the victim's private life.
2.
When the victim activates the link in the phishing message or opens the file attachments, the second part of the scam begins. Many want to take a closer look at the content and open the attachment, unwittingly installing malicious software (malware such as Trojans) or finding themselves on a fake website by clicking on the link. There, they try to log in with their real user name and password because the website looks deceptively real. The entries are saved by the criminals. Depending on the type of hijacked customer portal, the criminals can then act in the name of the victim, pass on sensitive data, debit money, place orders, lock the owner out of their account, send fraud messages to the victim's contacts, etc. The victim's account is then locked.
Phishing by email

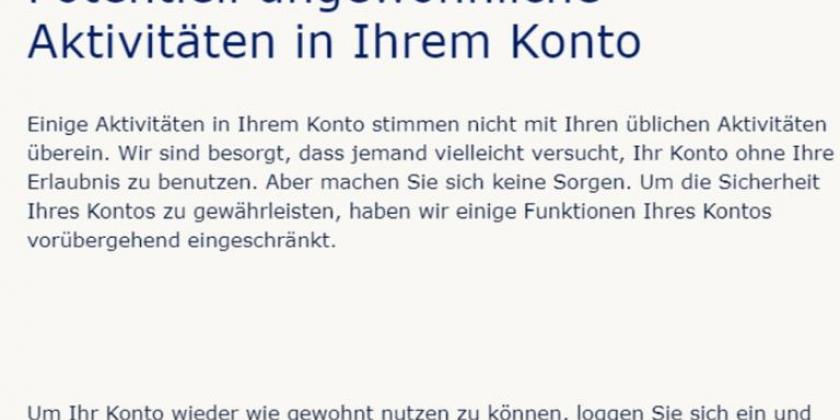
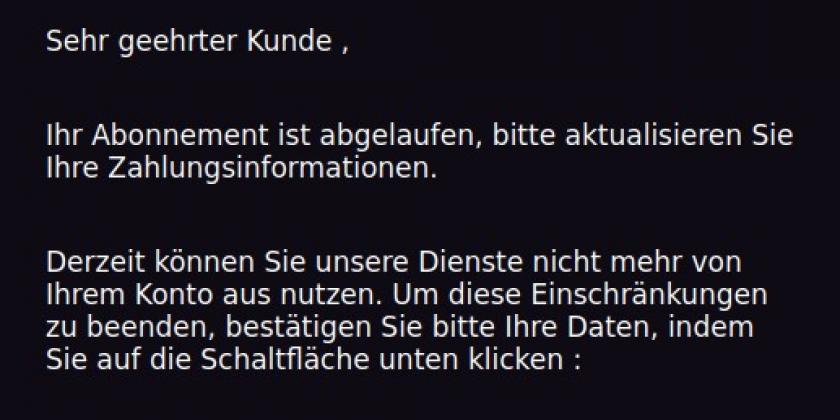
The most common method is deceptive phishing by email - the "classic" method using electronic mail can best be translated as "deceptive phishing". For example, if you are emailed about a competition, an inheritance, a problem in an account, a reminder or an undelivered parcel, and there is a link to open and view details - remain very sceptical! Cybercriminals are always finding new ways to get your attention.
- Sender is unknown: While it is not uncommon to receive an email from someone for the first time, especially if it is someone outside your company or circle of acquaintances, this can be the first sign of phishing. If you receive an email from someone you don't know, or if your mail programme identifies the contact as a stranger, take a moment to examine the email extra carefully.
- If you receive an email from someone you don't know, or if your mail programme identifies the contact as unknown, take a moment to examine the email extra carefully.
- Most phishing emails are sent en masse, so you are most likely to be addressed impersonally: For example, "Dear customer" or "Important message", etc.
- If data records about you have already been misused on the Internet, then you will be addressed personally in the phishing message. Ask yourself whether you are a customer of this company at all. Did you even take part in the action mentioned in the message? How did the other party get in touch with you? Personalised messages are more difficult to see through as a scam. If you come across such a personalised phishing attack with several details about you, check which of these details about you are freely available on the net. You should try to do something about this by limiting the visibility of this publicly available information.
- Mismatching email domains - If the email purports to be from a reputable company, but the email is sent from a different email domain such as gmail.com or gmx.at, which are used by private individuals, it is probably a scam.
- If you use several email providers at the same time and have registered with one customer portal with a certain email address, but now a message from the customer portal suddenly appears in the other email inbox, which is not linked to that customer portal at all, the probability of a phishing attempt is very high.
Example: Someone uses Gmail and GMX both for email traffic and has registered at IKEA with GMX. Doubtful message from IKEA reaches GMAIL inbox. - The message often threatens unpleasant consequences such as a penalty fee, account blocking or deletion, etc. if one does not react immediately or within a short period of time. Under stress and pressure, people become more careless and are more easily tempted to act rashly. For example, to open an unsafe link, a file attachment or to enter personal data. Do not let the alleged urgency push you into mindless behaviour!
- Another trick is to intentionally make the message look like a stray email. This message is made to look as if it has landed in your inbox unintentionally. It contains a link or file attachment to supposed information from the other person's sphere. This is aimed at the curiosity of the not "mistaken" email recipient. The criminals take advantage of the fact that the supposedly original recipients are more likely not to inquire as soon as their curiosity has been satisfied. When attempts are made in this way to trick senior management personnel, this special form of spear phishing is referred to as "whaling". The goal here is the "big fish".
- A clone phishing campaign is when fraudsters copy a genuine email and send their malicious clone, laced with malware, from a similar-sounding email address to the same group within a short period of time. These addressees are familiar with the genuine email and are particularly at risk, as they check the malicious, almost identical follow-up email less strictly and are more willing to open the file attachments it contains.
Dangerous email attachments
Messages with attached files require special caution - double check the trustworthiness of the sender! Check whether your virus protection is up to date and has analysed the file attachment. Particularly dangerous are executable (.exe .pif .bat .dll .scr) or compressed files (.zip .rar .7z ...) as phishers hide viruses and Trojans in them.
- In the meantime, phishers are no longer attaching malicious files directly to mails, as they could be detected by virus protection programmes. Instead, they store them on cloud services (e.g. Dropbox, Mega, Google Drive, OneDrive,...) and link these outsourced malicious files in the bait message. Of course, you should not download or open them.
- Phishers hide so-called executing scripts in macro elements in seemingly harmless office application formats (.doc, .docx, .xls, .xlsc, .xlsm, .pdf), which download and install malware in the background when opened. Even if you are asked by the operating system when opening an email attachment whether a macro should be executed, supposedly because the message was sent from a mobile device, your answer is no! The pretended reason is nonsense from a technical point of view!

General tips independent of the phishing medium
- The message often threatens unpleasant consequences such as a penalty fee, account blocking or deletion if one does not act immediately or within a short period of time. Under stress and pressure, people become careless and are more easily tempted to act rashly. For example, opening an unsafe link, a file attachment or sharing sensitive data.
- Have you been sent an official-looking message via an unusual method? Tax office reports via WhatsApp? Customs notification arrives by text message? Bank or credit card issuer writes to you on Instagram? Check the website of the genuine entity to see if it warns of a phishing wave and look there for information on which contact channels this institution or company never uses. Meanwhile, large companies regularly warn about the latest phishing waves on their portals. A call to the real office can also provide clarity. However, do not use the contact contained in the dubious message for your check!
- Pay attention to the internet address linked in the message - are the spelling of the company name and the internet address of the sender correct? Compare the address in the link in the message with the one they found themselves using his search engine in the browser. The phenomenon is called cyber-squatting, criminals occupy a similar sounding internet address (domain). They take advantage of the fact that potential victims do not pay close attention to whether the original or the fake copy with subtle differences in the domain name opens in the browser.
Examples: Instead of www.google.com you get to g00gle.com written with zeros instead of letters "o", instead of microsoft.com you get to rnicrosoft.com where the "m" has been replaced by an "r" and an "n". - Is the linked destination a secure website? (Internet address begins with https://) Encrypted pages are displayed in the browser with a lock symbol 🔒 in front of the address. Clicking on the lock symbol in the browser displays the certificate. If in doubt, do not follow the link!
- Pay attention to spelling and form errors in the text of the message! Fraud attempts in phishing waves from abroad are often translated incorrectly from other languages.
- Beware if you are asked to pay for something via the Google Play Store, with a cryptocurrency or an alternative payment method. Reputable companies do not accept Google Play credit cards and the like as a means of payment.
- Also beware of phishing attacks via wireless networks (WLAN or Wifi): Fraudsters use the script "wifiphisher" according to the following principle: The script imitates the WLAN in which users are logged on and sends so-called deauthentication packets in the name of this fake WLAN. These disconnect all connected devices (clients) from the real WLAN. The attackers speculate that someone will then try to connect automatically to the imitated WLAN. This is done on the phishing page of the fake access point. There, a reason is given for having to re-enter the WLAN password.
Smishing - Phishing through SMS

When phishing is attempted by means of SMS, it is called "smishing", a neologism made up of SMS and phishing. The difference here is the method of transmission. Instead of an email, the dubious request for action comes in the form of an SMS message. And it again contains a link that fraud victims are supposed to follow.
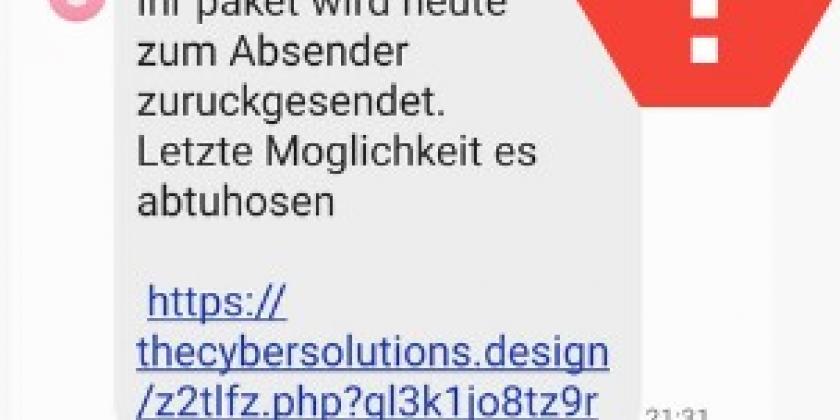
- Fake SMS often contain a link, which is a shortened internet address (URL) created with a URL shortener (e.g. bitly.com or tinyurl.com). This prevents victims from seeing the exact internet address and thus recognising that it is a fake sender.
- No telephone number of the sender is displayed. Instead, you see a generic designation such as "Delivery" on the display.
- The sender's telephone number may have a dubious country code (e.g. +913).
- The origin can be represented as a bank or parcel service, for example, and ask for the access data for the customer account in question. Such a fake is often formulated as a security question that cannot be postponed.
- A smishing message may also contain a call link that, when pressed by phone, connects you to a fraudulent call centre or to an expensive premium rate 0900 number.
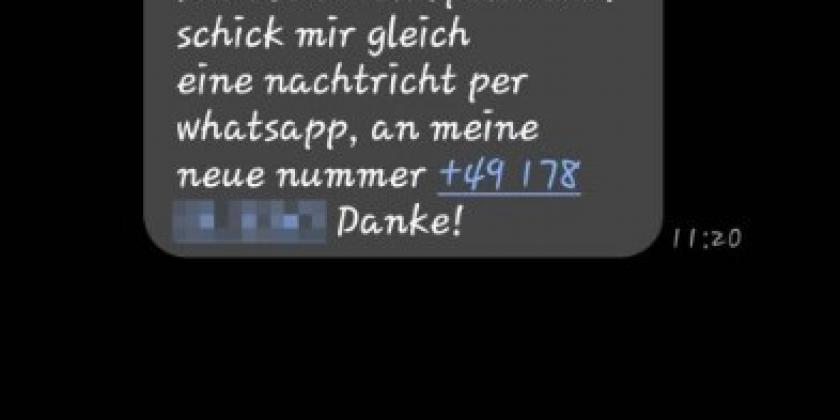
- Another trick is a text message, supposedly from a known person with a supposedly new number because of a mishap (accident or similar). The authenticity of the request for a quick aid payment or money loan can be quickly checked by making a control call to the real "old" number.
Vishing - Phishing by phone

When fraudsters call and pretend to be someone else, urging them to transfer money or give out logjn data, this is called "voice phishing" - or vishing for short. Before they pick up the phone, the display may even show them the familiar name of a company or government institution. However, this says nothing about the true identity of the caller.
Callers with malicious intent try to guide their victims to enter data on a fraudulent website or to persuade them to authorise payment, which is then received in a follow-up message. During the call, victims are put under pressure with psychological tricks, e.g. by raising fears of a security risk and by the fraudster presenting himself/herself as the solution to the problem. (e.g. as a Microsoft employee in the Windows support scam. In such phishing waves, over 10,000 fraud attempts are reported per month).
- Under no circumstances should you disclose bank or credit card details, authorise payments or follow the instructions during or after the call! Genuine employees of banking and payment services never ask for access data over the phone! Not even to call up the links contained in the follow-up message!
- In the case of vishing, the telephone number is usually disguised - the callers remain anonymous by calling with the number suppressed.
- Or the name of a company or institution (e.g. "Amazon Support" or "Police") is displayed instead of a telephone number. But this can be as fake as the call itself. The word or number on the screen when calling can be chosen and paid for with so-called spoofing services or even in apps based on Voice-over-IP (VoIP) techniques.
- The spoken German may not be very good or the call may be in English. The criminal call centres are often active in several countries.
Phishing on social media

Fake social media accounts are also increasingly used by cybercriminals to fish for information from potential victims and their circle of acquaintances. In addition to conventional bait messages, the circle of friends of a hijacked account can be attacked on a personal level via messenger messages from a social media account. In the next step, the trust of the supposedly known sender is abused.
On platforms such as Instagram, LinkedIn, Facebook or Twitter, these attacks usually occur after criminals have created another fake login page and use the usual method to grab login data. According to Norton Labs, almost three quarters of all phishing sites imitate Facebook in order to scam login data. Programming code and software toolkits for phishing, or to gain access to other people's social media accounts by means of brute force attacks (the programme runs and tries out possible entries endlessly until it succeeds), are also blatantly available on the public code platform Github, for example.
Another but less common method is a so-called "pay for followers" attack. This is aimed primarily at business social media accounts of companies. Victims are made a commercial-looking offer to increase the number of followers (subscribers) for a small amount of money. In the course of this fake offer, the login or credit card data of the "business customers" (victims) are again requested, allegedly for the purpose of implementation.
- Be particularly sceptical of unexpected messages from newly created accounts! Social media operators delete fraudulent accounts when many complaints about them have accumulated. Therefore, accounts created for the purpose of phishing usually do not have a long lifespan. Do not accept friend requests from complete strangers!
- A typical phishing message informs you of an alleged problem with your social media account. You are supposed to log in again to fix the problem. Update your data or respond to a contact request. The "handy" link to do this is included in the message. If this link does not lead to a page that contains the exact wording and domain ending of the platform (e.g. facebook.com) in the URL at the front, it is most likely a scam attempt.
- Do not use the same username and password for all accounts! This tip seems clear, but many do not follow it because they do not consider the value of their social media account or a potential threat (even to their own contacts) high enough.
New developments in phishing
- Multi Channel Phishing
The situation is exacerbated by the spread of phishing to new platforms. The more channels a private individual uses in addition to email, e.g. social media, SMS and apps, the more access points there are for criminals. Attacks are now often carried out via several media at the same time, as they appear more credible. For example, you receive a prompt notification via email and WhatsApp that there is a problem with a parcel delivery. Both may be fakes and allegedly link to a website with further details. If you fill in the input mask there with your access data, your identity will be stolen. Or if you download a file there, your device will be infected with malware.
- Misused AI tools
Software with generative artificial intelligence is becoming easier and easier to use and increasingly accessible to the public and online. Clearly, cyber criminals are also using these resources to make phishing attempts more perfidious. For example, through voice cloning and deepfakes, or simply through qualitative translations when a phishing wave from one language area is repeated in another. Until now, phishing attempts could be often recognised by grammatical or spelling mistakes. This is now becoming more difficult.
- Romance Scams
ChatGPT, stolen images and videos, as well as the fact that social media channels are becoming increasingly interconnected, make it much easier for criminals to make fake identities look more credible and attractive. When it comes to romance scams on social media or dating sites, fraudsters usually target advance fee fraud so that money is eventually transferred to them or things are bought for them. However, there is also the risk of identity theft. For example, by the flattered victim providing login data or agreeing to the installation of certain software (e.g. Anydesk) and losing control over programmes, accounts or even the entire computer system and the perpetrators accessing critical data themselves at will.
Phishing and pharming terms

The term phishing is composed of the English words password and fishing. The first letters PH come from the jargon of hackers, used for example in the spelling of the word phreak, a self-designation in the scene. Pharming, a further development of conventional phishing, is when malware is installed on the victim's device. In the sense of this imagery, the so-called "seed" is planted in order to "harvest" the stolen data later.
In this case, the cybercriminals have manipulated the host file on the end device and this then forwards to a fake page of the criminal hackers instead of the real website. The terms DNS spoofing, cache poisoning or DNS hijacking are commonly used for such malicious redirection. In the past, for example, it was abused that users were shown a search page of their internet provider instead of an error message of the browser. If this page runs via a name server that is independent of the real provider, sensitive data can be accessed without the knowledge of the provider. Unfortunately, there is another even more disturbing method: DNS servers on the provider side are directly infected in order to redirect a large number of users to the fake website, where they are infected with malware or unknowingly enter sensitive (financial) data. Generally speaking, DNS servers control web traffic by converting browser requests into physical IP addresses from which web content is retrieved. End users can no longer prevent such a provider-corrupted DNS server redirection even by manually entering an internet address, even if their device is completely free of malware, because the redirection happens automatically on the server side with every connection request. In such a case, only the DNS operators can provide a remedy. Fortunately, this method requires advanced hacking skills. The DNS hosts and providers have learned to use special protection programmes and this method against "normal" phishing victims is usually not worth the effort for the criminals. If you are careful in general however, you can avoid the common phishing attacks described in the article above!
Defensive measures against phishing
Image gallery - Phishing examples
Links
Watchlist Internet explains phishing, smishing, vishing
https://www.watchlist-internet.at/news/phishing-smishing-vishing-so-schuetzen-sie-sich-vor-datendiebstahl/
Online Threat Alerts - international community that has been issuing phishing alerts since 2012
https://www.onlinethreatalerts.com/
Cloudfare lists the 50 most frequently imitated company names in phishing
https://blog.cloudflare.com/50-most-impersonated-brands-protect-phishing/